Daniel Grießhaber over hackaday.io created a project called ESPTool. It is a tool to test WiFi networks security and to demonstrate how easy it is to crack a WiFi password or jam a WiFi network. Daniel designed ESPTool for education and self-test purpose.
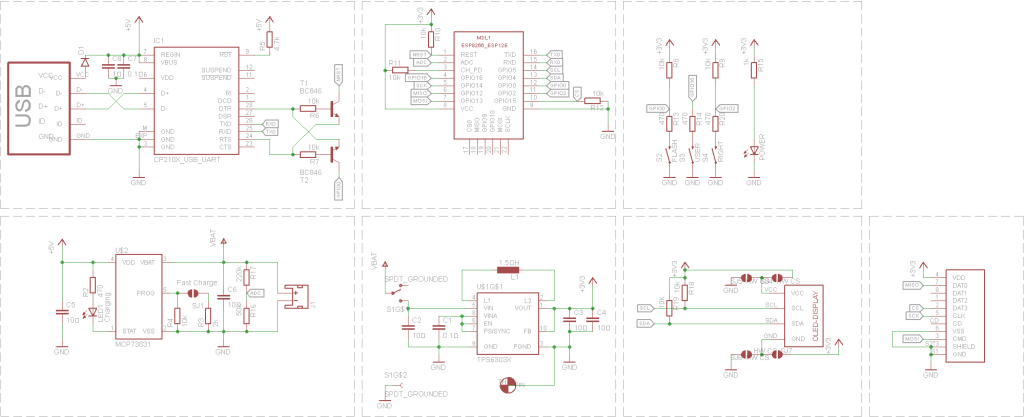
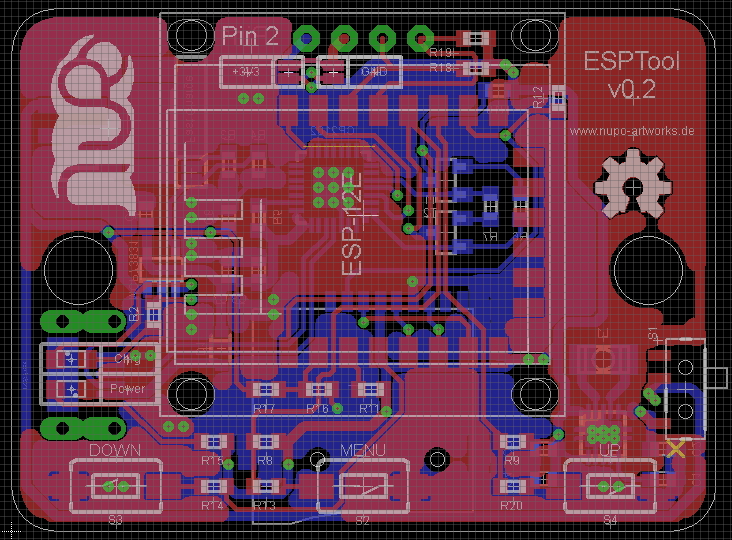
The Device has SSD1306 based OLED display, microSD card socket, 3 general purpose buttons, ESP8266-12E module, TPS63031 Buck-/Boost converter with an input range from 1.8V – 5.5V, MCP73831 Single-Cell LiPo Charger Chip and CP2012 USB to UART converter chip.
The firmware of ESPTool has the following layers of attacks, according to Daniel’s documentation:
- Layer 1:
Since the ESPs Radio is not really configurable, it is not possible to create a WiFi Jammer that works by emitting broadband noise or any other Layer 1 attacks.
- Layer 2:
- Deauthentification attack
- Collecting authentication frames and save the keys to SD card for later decryption (using a wordlist on a computer, the ESP neither has enough memory nor enough processing power to crack them on the system)
- arp spoofing and session hijacking when connected (needs investigation)
- evil twin hotspot
- Layer 3 (after connecting to an AP):
- Host discovery (IP Scanner)
- Ping flooding (ICMP Pings)
- Layer 4 (after connecting to an AP):
- Port Scan on Host
The source code and the design files, using Eagle CAD, (SCH & BRD) can be found here.
[Project page over hackaday.io]