Before talking about OpenTitan and Microsoft Pluton – two security chips by two tech giants, let’s have an overview of what security chips actually are.
Today, the hardware-level security of an operating system is an extremely important matter and is taken very seriously by manufacturers. The core security of an operating system depends on a chip separate from the CPU. This chip is called TPM or Trusted Platform Module. TPM stores various keys and other sensitive information that saves the integrity of the entire system. Security chips are also used in embedded platforms where security is the utmost priority. A good example is IoT based smart home control system. If an attacker gets access to the secure keys of various APIs used for controlling “things” remotely, they can do anything. So, these types of keys are stored in TPM.
Silicon Root of Trust (RoT) chips can provide many security benefits by helping to:
- Ensure that a server or a device boots up with the correct firmware and hasn’t been infected by low-level malware.
- Provide a cryptographically unique machine identity, so an operator can verify that a server or a device is legitimate.
- Protect secrets like encryption keys in a tamper-resistant way even for people with physical access (e.g., while a server or a device is being shipped).
- Provide authoritative, tamper-evident audit records and other runtime security services.
Google OpenTitan
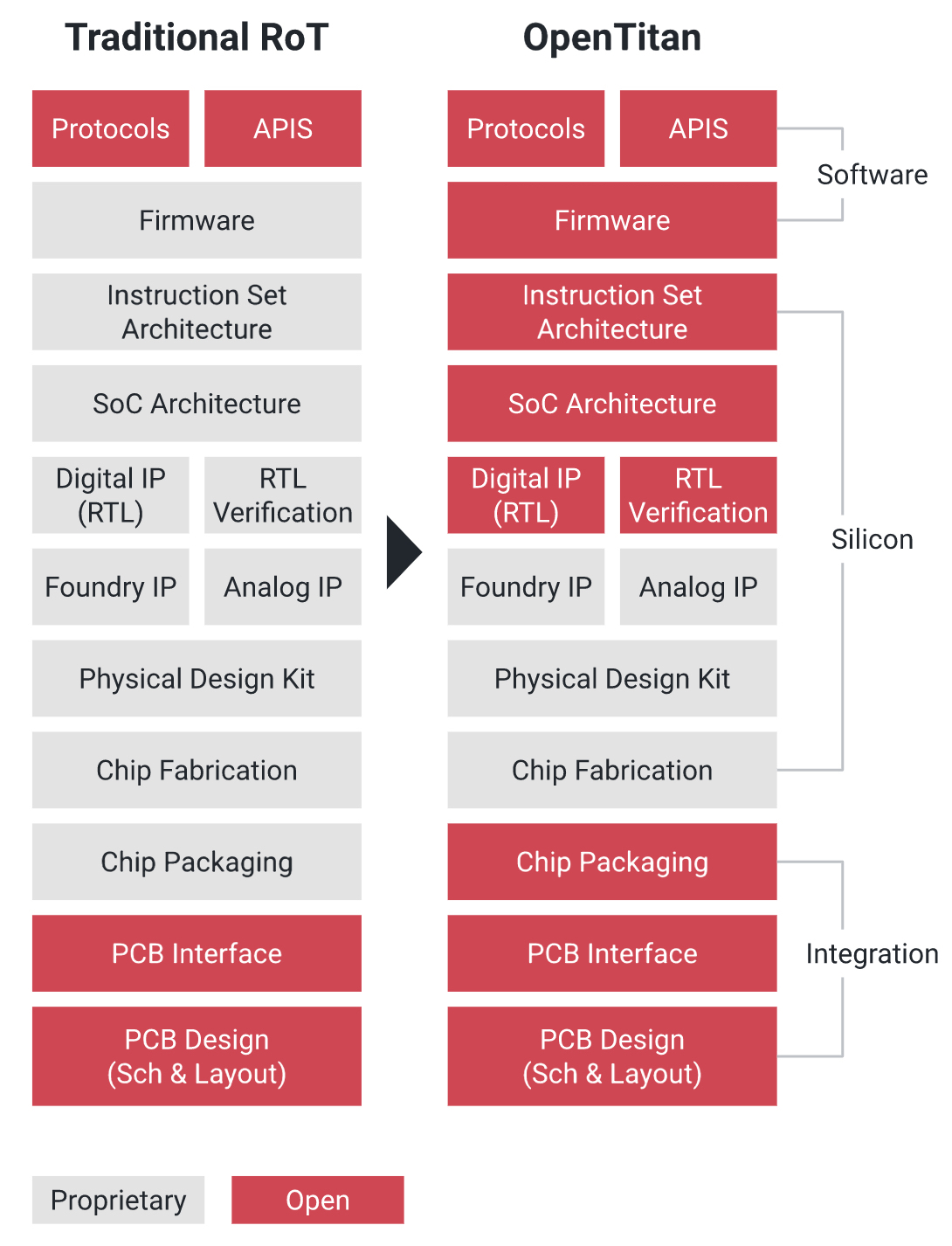
OpenTitan is the first open-source project building a transparent, high-quality reference design and integration guidelines for silicon root of trust (RoT) chips (such as TPMs). The main goal of OpenTitan is to make the silicon RoT design and implementation more transparent, trustworthy, and secure for enterprises, platform providers, and chip manufacturers. Big companies like Western Digital, Seagate, Nuvoton, etc. are partnering with Google in this project.
OpenTitan being open-source, Root of Trust chip designers can embed this in their design with little or no legal complexities. Also, numerous talented developers can contribute to this project and raise the security standard. Open-source silicon can enhance trust and security by design and implementation transparency. problems can be detected early, and bugs can be fixed. This will also provide implementation choices and preserve a set of common interfaces.
As per google, The OpenTitan project follows three key principles:
- Transparency – anyone can inspect, evaluate, and contribute to OpenTitan’s design and documentation to help build more transparent, trustworthy silicon RoT for all.
- High quality – we are building a high-quality logically-secure silicon design, including reference firmware, verification collateral, and technical documentation.
- Flexibility – adopters can reduce costs and reach more customers by using a vendor- and platform-agnostic silicon RoT design that can be integrated into data center servers, storage, peripherals, and other devices.
The following image shows the key differences between a traditional RoT design and OpenTitan:
Microsoft Pluton
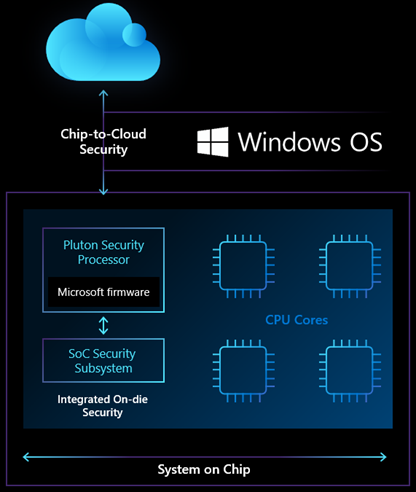
Even though TPM is the most commonly used RoT, there is one big problem – TPM lives outside of the main processor. An attacker with physical access to the computer can use a logic analyzer to steal information from the bus interface between the security processor and the main CPU. They can also modify the information using sophisticated attack techniques. So, with Pluton, Microsoft removes the potential for that communication channel to be attacked by building security directly into the CPU. In this way, it is almost impossible to tap the communication channel between the RoT and the CPU. Pluton is designed in collaboration with leading silicon partners AMD, Intel, and Qualcomm Technologies, Inc. So, processors made by these chip-designers will have Pluton security chip built-in.
Windows PCs using the Pluton architecture will first emulate a TPM that works with the existing TPM specs and APIs. This will enable customers to benefit from enhanced security for Windows features that rely on TPMs like BitLocker and System Guard. Even when an attacker has installed low-level malware or has physical access to the hardware, the secure information stored in Pluton cannot be removed. This is achieved by storing sensitive data like encryption keys securely within the Pluton processor, which is isolated from the rest of the system.
Conclusion
OpenTitan and Pluton have the same goal but with different philosophies. Both want to improve Root of Trust but google focuses to design an open standard for RoT design while Microsoft targets to embed RoT into the CPU to enhance Windows security. Both of them have the potential to be the future of security chips. Till now, neither OpenTitan nor Pluton has announced any specific processor that features either of them. Also, there’s is no release date available.
image source: depositphotos.com