Jasper Devreker, a computer science student at Ghent University, is working to make the ESP32 truly open-source by reverse-engineering a WiFi MAC layer for the ESP32.
We know the ESP series for its exceptional price-to-performance ratio, and it also includes ESP-IDF, the open-sourced framework and toolchain for ESP-based controllers. You can modify your code to some extent, but you cannot alter the code for the RF part, mainly the Wi-Fi and Bluetooth because they are distributed as binaries with the ESP-IDF.
The solution to this problem is straightforward: Reverse Engineering. By reverse engineering the wireless part you can have full control over the radio module of the ESP-32. with that in mind developers, like Devreker, are building upon the work initiated by Uri Shaked in 2021 and Martin Johnson in 2022.
Devreker explains,
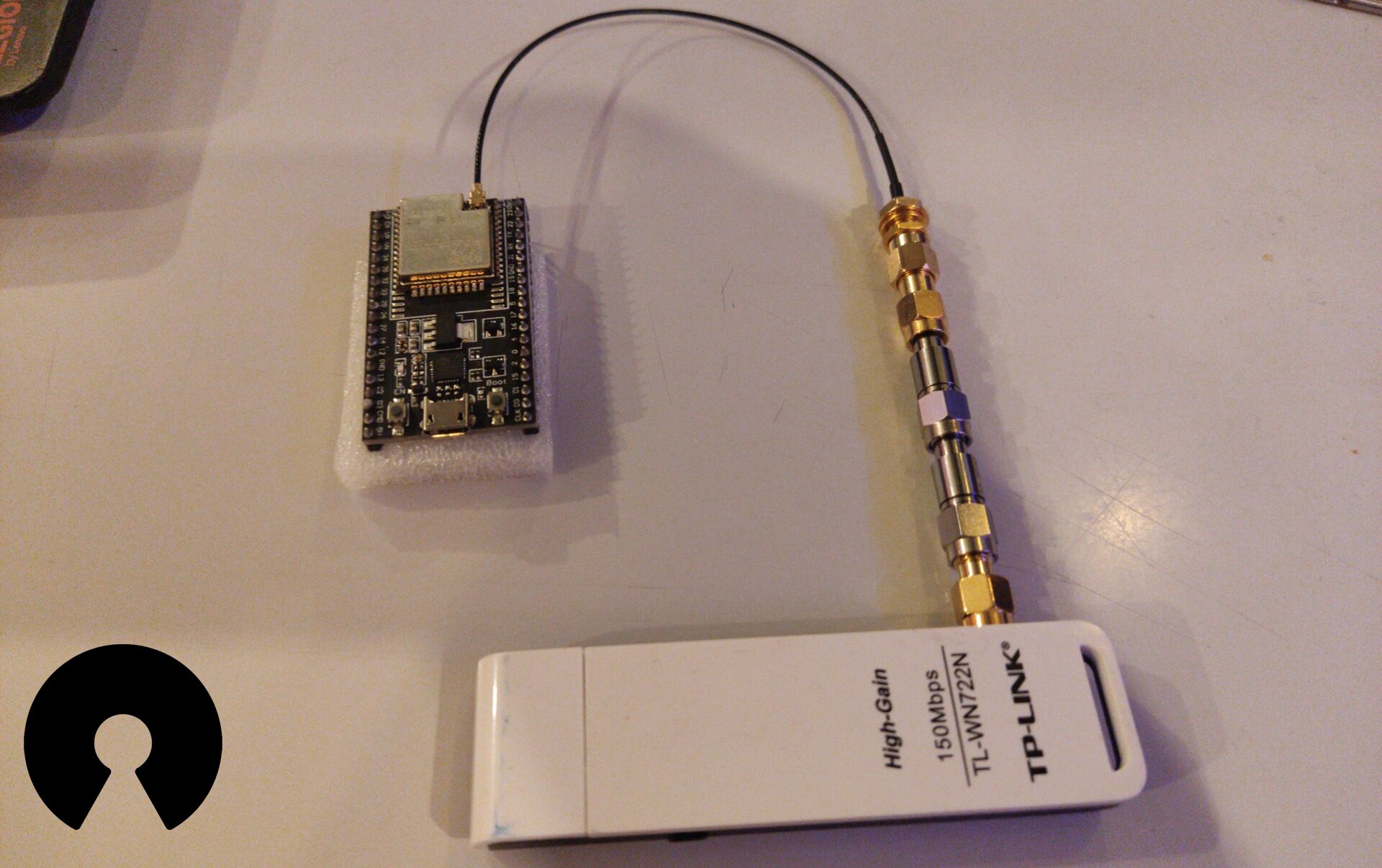
We connect [the] antenna connector to a 60dB attenuator (this weakens the signal by 60dB),” Devreker continues, “then connect that to the antenna connector of the wireless dongle. That way, we’ll be able to receive only the packets coming from the ESP32, and the ESP32 will only receive packets sent by the wireless dongle.
By placing the device in a Faraday cage and using the mentioned method, they analyzed the hardware’s lifecycle during packet transmission. This led to the development of proof-of-concept firmware, enabling independent packet transmission and reception without relying on Espressif’s SDK.
That is an impressive feat, but the initialization code still depends on Espressif’s code blob. However, Devreker and his team say that when the reverse-engineering process is complete, they will be able to implement channel switching, data rate adjustment, TX power control, and an open-source WiFi initialization sequence.
In the long term, the focus will be on enhancing features such as modem power saving by turning off the modem when idle, implementing AMSDU, AMPDU, HT40, QoS, moving WPA2 cryptography from software to hardware, adding Bluetooth support, and creating SVD documentation for all reverse-engineered registers.
The complete project details are on Ghent University’s Zeus WPI website, including a post about the packet-reception breakthrough. The source code is available on GitHub under the MIT license. You can also check out Hackster or CNX-Software posts for additional information.