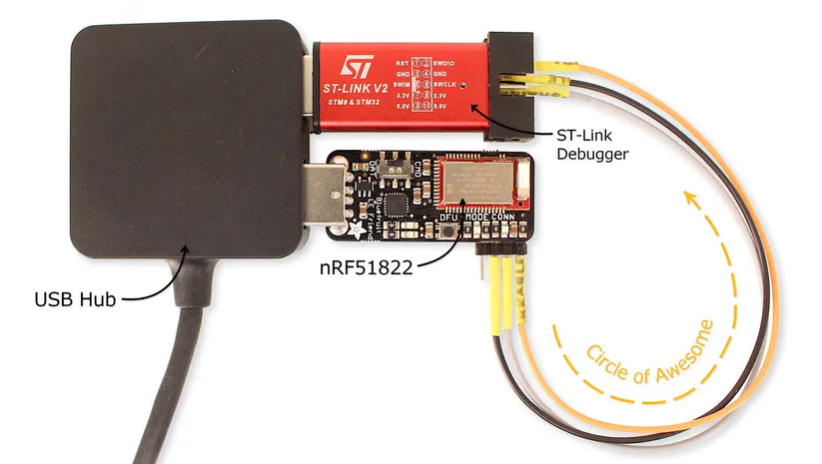
Loren Browman, a security analyst recently published a guide to automated unlocking of Nordic Semiconductor’s nRF51-series systems-on-chips (SoCs) which claims to be protected, enabling a full memory dump or interactive debugging regardless of protection settings. In a blog piece for security firm Optiv, Loren Browman writes
“Recently, while conducting an assessment for a product based on the nRF51822 System on Chip (SoC), I found my target’s debug interface was locked — standard stuff… Reading up on the nRF51 series SoCs revealed that this is how these chips are designed. It’s always possible to perform a full memory recovery/dump, even if read back protection is enabled.”
He continue:
“I wanted to build on what others have discovered, extending the attack to completely and automatically bypass the memory protection mechanism offered by these SoCs. Beyond reading memory, I also wanted to unlock the device to support interactive debug sessions with my target.”
This resulted to nrfsec, which is an open source research security tool published under the GNU General Public License 3, used for unlocking and reading memory on nrf51 series SoCs from Nordic Semiconductor.
Features of the nrfsec includes:
- Read all target memory, bypassing the Memory Protection Unit (MPU) settings with integrated read gadget searching.
- Automated unlock feature: read all program and UICR memory, erase all memory, patch UICR image, reflash target into unlocked state.
- Boot delay command flag for interacting with target prior to performing memory read, allowing for RAM dumps.
- All firmware images are saved for importing into your favorite disassembler.
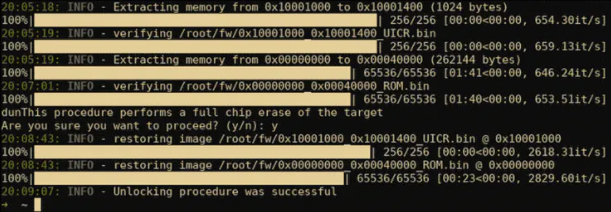
About nrfsec, Loren Browman says
“[nrfsec] can automate the entire outlined process for you… Letting you uncover the internal working of any nRF51 based product.” Once it is unlocked, the tool establishes a debug session to the now-unprotected SoC. For installation, nrfsec is built on the pyswd library and currently only works with the ST-Linkdebugging interface.
nrfsec requires python 3.7+ to run and can be installed with pip. For nrfsec to work, it will first of all make a quick info check to ensure that nrfsec is able to communicate with both the debugger and the target. The output for the info will also specify if the target is currently locked with some additional interesting target information. Then nrfsec will automatically find a useable read gadget and dump all memory on a locked target. If the target is not already locked, you can issue the lock sub-command, and it will lock the again. If you want to unlock the target, you issue the unlock sub command which will perform the following steps:
- Read all memory regions (most importantly, ROM and UICR) and save the images.
- Perform a full target erase, this will enable writing to the UICR again.
- Patch the UICR image extracted during step 1 to disable read back protection.
- Re-flash the ROM and patched UICR back to the target.
More details of how the tool works and how to use it can be found on the Optiv blog, while nrfsec itself is available to download from GitHub, or can be installed from the pip Python package manager.












Technology is really evolving in to a whole new level.